
Table of Contents
- Introduction
- The Digital Age: A Blessing and a Curse
- Why Cybersecurity Matters
- Basic Concepts of Cybersecurity
- Cybersecurity Best Practices
- Conclusion
In an increasingly interconnected world driven by technology, the term “cybersecurity” has become a buzzword. It’s not just a concern for IT professionals or large organizations; it’s something that every individual must be aware of in the digital age. This article aims to demystify the concept of cybersecurity, explain its significance, and emphasize why everyone, regardless of their technical background, must understand and practice it to stay safe and secure online.
Introduction
Cybersecurity, a portmanteau of “cybernetics” and “security,” is the practice of protecting digital systems, networks, and data from unauthorized access, damage, or theft. It’s a concept that has gained immense importance as our lives have become increasingly intertwined with digital technology. From online banking to social media, from smart home devices to e-commerce, the digital age has brought incredible convenience but also significant risks.

The Digital Age: A Blessing and a Curse
The digital age, often celebrated for its transformative potential and vast array of conveniences, has revolutionized the way we live, work, and connect with the world. It has brought an unprecedented level of convenience and accessibility to various aspects of our lives, offering remarkable opportunities and capabilities that were once unimaginable.
In this era, we can effortlessly communicate with friends and family across the globe in an instant, bridging geographical divides and fostering connections that were once limited by distance. We can conduct complex financial transactions, from payments to investments, without the need to visit a physical bank branch, simplifying our daily financial activities. Furthermore, the boundless information available at our fingertips has democratized knowledge and learning, allowing us to explore virtually any subject, access educational resources, and stay informed about current events with remarkable ease.
However, beneath the veneer of this digital utopia lies a complex and multifaceted reality. The very conveniences that define the digital age also introduce a myriad of new challenges and threats. Cybercriminals, hackers, and malicious actors are quick to exploit the vulnerabilities inherent in our digital existence. Their motives are diverse, ranging from financial gain through fraudulent activities and extortion to espionage with potentially catastrophic national security implications.
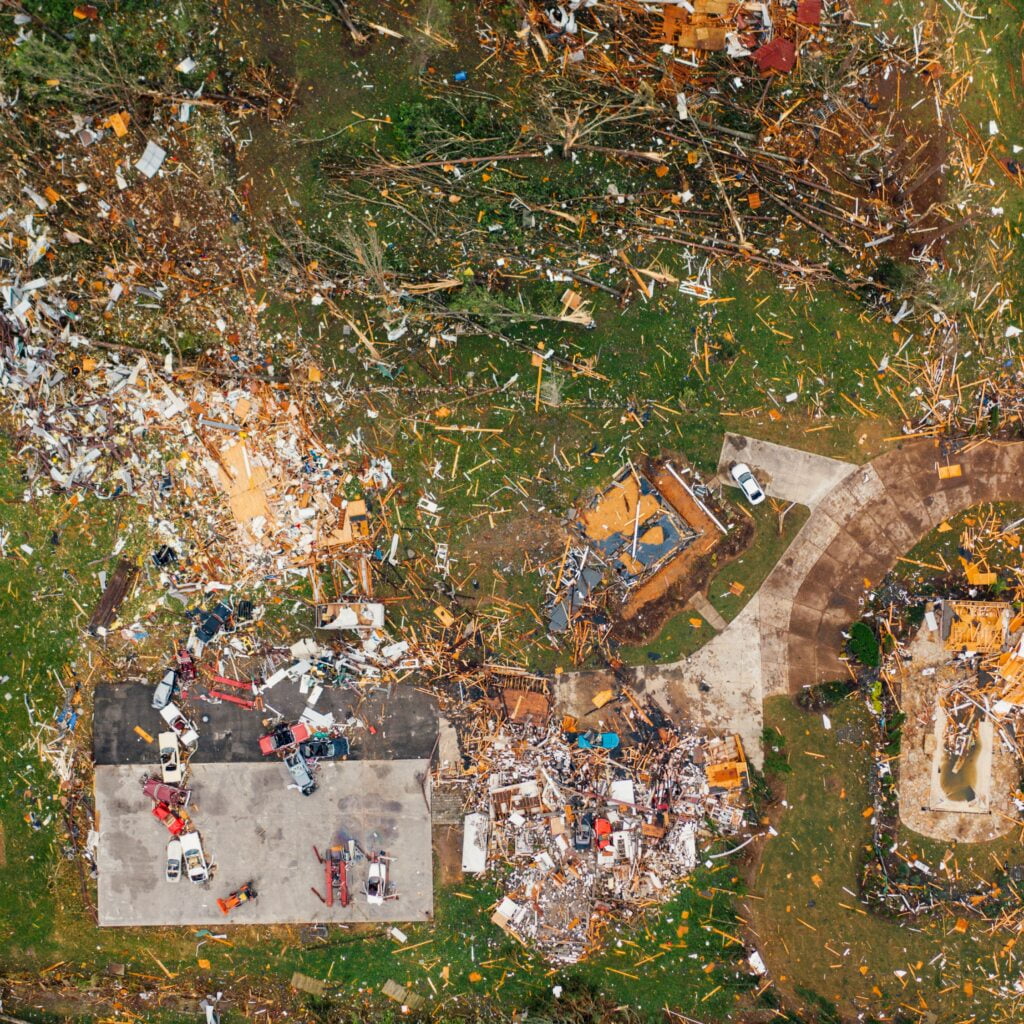
The consequences of these cyberattacks can be staggering, encompassing a wide spectrum of personal, economic, and even geopolitical ramifications. At the personal level, stolen personal information can lead to identity theft, financial loss, and the invasion of one’s privacy. Victims may find their bank accounts emptied, their personal data sold on the dark web, or their lives disrupted by the far-reaching effects of cybercrimes.
On a broader scale, the economic impact of cyberattacks on businesses and organizations is profound. Data breaches can result in substantial financial losses, damage to a company’s reputation, and the theft of sensitive customer and business data. This not only affects the company itself but can also reverberate through the economy, potentially leading to job losses and market instability.
Perhaps even more alarming is the vulnerability of national security in the digital age. State-sponsored cyberattacks can target critical infrastructure, military systems, government secrets, and even elections. These attacks can pose a significant threat to a nation’s sovereignty, security, and interests, with implications that reach far beyond the digital realm. National cybersecurity has emerged as a pivotal component of defense and security strategy in the modern era, as it safeguards classified information and the integrity of critical military infrastructure.
In summary, the digital age is undoubtedly a double-edged sword, offering unparalleled opportunities while introducing a host of risks that demand our vigilance and preparedness. Understanding the intricate interplay between the benefits and challenges of this digital revolution is crucial for navigating the complexities of the modern world. It’s a world where the seamless flow of information, wealth, and connections is accompanied by the ever-present shadows of cyber threats and vulnerabilities.
Why Cybersecurity Matters
1. Personal Privacy
In today’s digital age, we entrust a vast amount of personal information to the online world. This includes details on our social media profiles, email accounts, personal preferences, and even sensitive health-related data. Our digital footprint is extensive and, in many ways, mirrors our real-world identity. Without robust cybersecurity measures, this information is at risk of falling into the wrong hands. Cybersecurity is crucial for preserving personal privacy by preventing unauthorized access, data breaches, or identity theft.
The potential consequences of a privacy breach extend far beyond the online realm. Sensitive information can be exploited for various malicious purposes, from financial fraud to impersonation. With effective cybersecurity, individuals can maintain control over their personal data and keep it out of the reach of cybercriminals.
2. Financial Security
The digital transformation has drastically altered the way we manage our finances. Online banking, e-commerce, and digital payment systems have brought unparalleled convenience to our lives. However, this convenience also introduces risks. Cybersecurity is the safeguard that stands between our financial transactions and the threat of unauthorized access, fraudulent activity, and data breaches.
Without robust cybersecurity in place, individuals risk losing money, having their financial information stolen, or becoming victims of scams. Cybercriminals often target financial accounts and transactions, making it essential for everyone to prioritize cybersecurity to ensure the safety and security of their financial assets.
3. Identity Theft
Identity theft is one of the most severe and distressing consequences of poor cybersecurity. Cybercriminals have the capability to pilfer personal information, including social security numbers, driver’s license details, and financial data, and use this information for fraudulent activities. These activities can range from opening credit accounts in the victim’s name to filing fraudulent tax returns.
Effective cybersecurity practices serve as a robust defense against identity theft. Through secure practices, such as strong and unique passwords, two-factor authentication, and vigilant monitoring of personal accounts, individuals can significantly reduce the risk of identity theft and protect their financial and personal reputation.

4. Protecting Critical Infrastructure
Beyond individual safety, cybersecurity plays a pivotal role in safeguarding critical national infrastructure. Sectors such as power grids, transportation systems, healthcare facilities, and communication networks rely heavily on digital technology for operations and efficiency. A breach in their cybersecurity defenses could have dire consequences.
For instance, a cyberattack on a power grid could lead to widespread blackouts, affecting millions of people and critical services. Attacks on healthcare facilities could compromise patient data and disrupt patient care. Ensuring the security of these systems is not just a matter of personal safety but also a matter of national security.
5. Business and Economic Impact
Cyberattacks on businesses have far-reaching consequences. They can result in significant financial losses, damage to a company’s reputation, and the theft of sensitive customer and business data. The implications of a data breach can be devastating for businesses of all sizes. Financial losses can include the cost of investigating the breach, compensating affected individuals, and implementing security improvements.
Moreover, the loss of sensitive business data can lead to intellectual property theft, disrupting business operations and reducing competitiveness in the market. A damaged reputation can result in the loss of customers and business partnerships. In severe cases, businesses may face lawsuits and regulatory penalties. Ultimately, the impact of cyberattacks on businesses has broader economic ramifications that can extend to job losses and market instability.
6. National Security
In today’s interconnected world, nations are not immune to the dangers of cyberattacks. State-sponsored cyberattacks can target critical infrastructure, military systems, government secrets, and even elections. These attacks can have severe geopolitical implications, jeopardizing a nation’s sovereignty, security, and interests.
Strong cybersecurity measures are essential for safeguarding national interests. They help protect classified information, critical military infrastructure, and the integrity of elections. By securing national cybersecurity, governments can reduce the vulnerability of their critical systems to foreign and domestic threats and promote a safer and more stable global landscape. Cybersecurity has become a crucial component of national defense and security strategy in the modern era.

Basic Concepts of Cybersecurity
To understand cybersecurity, let’s explore some fundamental concepts:
1. Cyber Threats
Cyber threats encompass a wide range of risks and potential dangers that can jeopardize the security of our digital systems, networks, and data. These threats manifest in various forms, each with its unique characteristics and objectives:
- Malware: Malware, short for malicious software, is a term used to describe any software specifically designed to harm or exploit computer systems. This category includes viruses, worms, Trojans, spyware, and ransomware. Malware can infect a device or network and compromise data integrity, confidentiality, and availability.
- Phishing: Phishing attacks are social engineering tactics aimed at tricking individuals into revealing sensitive information, such as login credentials, credit card numbers, or personal details. Cybercriminals typically send deceptive emails or messages that appear to come from trustworthy sources to lure victims into taking actions that benefit the attacker.
- Ransomware: Ransomware is a type of malware that encrypts a victim’s data, rendering it inaccessible. The attacker then demands a ransom payment to provide the decryption key. It can result in significant financial losses and data breaches.
- Social Engineering: Social engineering involves manipulating individuals into divulging confidential information or performing actions that compromise security. It relies on psychological manipulation, and common tactics include pretexting, baiting, and tailgating.
Understanding the various forms of cyber threats is essential because it enables individuals to recognize potential risks and employ appropriate defensive measures to protect themselves and their digital assets.
2. Vulnerabilities
Vulnerabilities represent weaknesses in a system that could be exploited by cybercriminals to compromise its security. These weaknesses may exist in software, hardware, or even human behavior. Some key points about vulnerabilities include:
- Software Vulnerabilities: Software vulnerabilities are flaws or weaknesses in computer programs, applications, or operating systems. Cybercriminals can exploit these vulnerabilities to gain unauthorized access, disrupt services, or compromise data. It is vital to keep software up to date by applying security patches and updates to address known vulnerabilities.
- Hardware Vulnerabilities: Hardware vulnerabilities can manifest as design flaws or weaknesses in computer hardware components. For example, microprocessor vulnerabilities like Meltdown and Spectre exposed weaknesses in chip architecture that could be exploited by attackers.
- Human Factors: Vulnerabilities are not limited to technology. Human behavior can also introduce vulnerabilities. These can include poor password choices, sharing login credentials, or falling for social engineering tactics. Awareness and training are essential for mitigating these types of vulnerabilities.
Mitigating vulnerabilities requires a proactive approach that involves identifying weaknesses, implementing security patches, and following best practices for software and hardware maintenance.
3. Attack Vectors
Attack vectors represent the paths or methods that attackers use to compromise a system, network, or individual. Understanding these vectors helps individuals and organizations defend against cyber threats:
- Email Attachments: Cybercriminals may send malicious attachments via email. Opening these attachments can result in malware infection. Always exercise caution when opening attachments from unknown or unsolicited sources.
- Infected Websites: Cyber attackers can compromise legitimate websites, making them distribute malware to unsuspecting visitors. Maintaining up-to-date web security and using web filtering tools can help protect against this type of attack.
- Unsecured Wi-Fi Networks: Unsecured or poorly secured Wi-Fi networks can be exploited by hackers to intercept data or launch attacks. When using public Wi-Fi, be cautious about the information you transmit, and consider using a Virtual Private Network (VPN) for added security.
Understanding attack vectors is critical for recognizing potential threats and taking appropriate precautions.
4. Countermeasures
Countermeasures are proactive actions taken to protect against cyber threats. These measures are fundamental to enhancing cybersecurity and include:
- Antivirus Software: Antivirus software scans for and removes malware from a computer or network. It’s essential for identifying and neutralizing threats.
- Firewalls: Firewalls act as a barrier between a private network and the internet. They filter incoming and outgoing network traffic, allowing or blocking data based on a set of security rules.
- Intrusion Detection Systems (IDS): IDS monitor network traffic for suspicious activities or known attack patterns. When they detect a potential threat, they trigger alerts or take preventive actions.
- Regular Data Backups: Regularly backing up data to external devices or secure cloud services is crucial for disaster recovery. In the event of data loss due to malware or hardware failure, backups ensure data can be restored.
Implementing these countermeasures is vital for protecting digital systems and networks from cyber threats.
5. Awareness
Cybersecurity awareness involves understanding the risks and best practices for online safety. It includes:
- Recognizing Phishing Emails: Being able to identify phishing emails is crucial. Look for signs like suspicious email addresses, unexpected requests for personal information, or messages that create a sense of urgency.
- Using Strong Passwords: Creating strong, unique passwords and avoiding password reuse across multiple accounts helps prevent unauthorized access.
- Cautious Online Behavior: Practicing caution when sharing information online and limiting oversharing on social media can reduce your exposure to cyber threats.
Cybersecurity awareness is a foundational aspect of personal and organizational security. By staying informed and vigilant, individuals can minimize the risks associated with the digital age and contribute to a safer online environment.

Cybersecurity Best Practices
To stay safe in the digital age, it’s essential to follow these cybersecurity best practices:
1. Strong Passwords
One of the fundamental pillars of online security is the use of strong and unique passwords for each online account. A strong password typically consists of a combination of upper and lower-case letters, numbers, and special characters. The purpose of a strong password is to make it difficult for malicious actors to guess or crack it. Using different passwords for different accounts is crucial because if one account gets compromised, it won’t impact your other accounts. To manage multiple complex passwords, you can consider using a password manager. A password manager securely stores and autofills your passwords, making it easier to maintain strong and unique credentials.
2. Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) is a security mechanism that adds an additional layer of protection to your online accounts. In addition to your password, 2FA requires a second form of verification, which can be something you know (like a PIN), something you have (like a smartphone or a security token), or something you are (biometric data like fingerprint or facial recognition). Enabling 2FA on your accounts makes it significantly harder for unauthorized individuals to access your accounts, even if they somehow obtain your password.
3. Regular Software Updates
Keeping your operating system, software, and applications up to date is crucial for maintaining a secure digital environment. Updates often include patches and fixes for known vulnerabilities that cybercriminals may exploit. Cybersecurity researchers and software developers continuously identify and address security weaknesses. By regularly updating your software, you ensure that you have the latest security patches installed, reducing the risk of falling victim to known vulnerabilities.
4. Be Cautious of Phishing
Phishing is one of the most prevalent and effective cyberattacks. It typically involves malicious actors sending fraudulent emails or messages that appear to come from legitimate sources. The goal is to trick you into revealing personal information or clicking on malicious links. To protect yourself from phishing attacks, it’s essential to learn how to recognize the signs of phishing attempts. Look for email addresses or URLs that seem suspicious or are slightly misspelled, and be skeptical of unsolicited requests for personal or financial information. Avoid clicking on links or downloading attachments from unknown or suspicious sources.

5. Secure Your Wi-Fi
Your home Wi-Fi network is a critical point of entry for potential cyber threats. To secure your Wi-Fi, it’s crucial to change the default password provided by your Internet Service Provider (ISP) to a strong, unique one. Additionally, enable WPA3 encryption, which provides a high level of security for your wireless network. Avoid using public Wi-Fi networks for sensitive transactions whenever possible, as public Wi-Fi networks are often less secure and can be targeted by cybercriminals.
6. Back Up Your Data
Data loss can happen due to various reasons, such as hardware failure, malware attacks, or accidental deletion. Regularly backing up your important data to an external device or a secure cloud service is a crucial practice. This ensures that you can recover your data in case of an unexpected event. Set up automatic backups to ensure you don’t forget to back up your data regularly. Make sure your backups are encrypted and stored securely to protect your sensitive information.
7. Monitor Your Online Presence
Your online presence includes social media profiles, email accounts, and other online services. Regularly reviewing and managing your online accounts and privacy settings is important. Ensure that your personal information is not publicly accessible when it should be private. Be mindful of what you share on social media platforms, as oversharing can make you a potential target for cyberattacks.
8. Learn Continuously
Cybersecurity is a dynamic field that evolves rapidly as new threats emerge. Staying informed about the latest threats and security best practices is essential. Follow reputable cybersecurity news sources and blogs to stay up-to-date. Consider taking online courses or attending webinars to expand your knowledge. By staying informed, you can adapt to the changing threat landscape and better protect yourself in the digital age. Remember that cybersecurity is a shared responsibility, and every individual’s efforts contribute to a safer online environment.
Conclusion
In the digital age, cybersecurity is no longer the sole responsibility of IT professionals or government agencies. It’s a shared responsibility that every individual must embrace. By understanding the basics of cybersecurity, recognizing the importance of online safety, and following best practices, we can protect ourselves and our digital lives from the ever-present threats in the digital age. In a world where our personal and financial information is increasingly stored online, knowledge of cybersecurity is not just a recommendation; it’s a necessity for a safe and secure digital existence. Stay informed, stay vigilant, and stay safe in the digital age.
BOaCaMlzSTuReOedfRDyCnYBkqQld
ujOlijJKWIqQuNrwJFeHcrEiL
[…] entrepreneurs navigating the competitive landscape, copywriters bring a distinct advantage. Crafting persuasive messages that convey brand essence, […]
Absolutely, and thank you for underscoring the unique advantage that copywriters bring to entrepreneurs in navigating the competitive landscape. Crafting persuasive messages that authentically convey a brand’s essence is indeed at the core of what we do. If you have any specific questions or if there’s a particular aspect you’d like to explore further, I’m here to help. Your engagement and insights are truly appreciated!
[…] entrepreneurs navigating the competitive landscape, copywriters bring a distinct advantage. Crafting persuasive messages that convey brand essence, […]
Thank you for recognizing the distinct advantage that copywriters bring to entrepreneurs navigating the competitive landscape. Crafting persuasive messages that convey the essence of a brand is a key aspect of what we do. If you have any specific questions or if there’s a particular aspect of copywriting you’d like to explore further, feel free to share. I’m here to continue the conversation and provide more insights into the world of effective messaging!